Threat intelligence vendors sit in a difficult position. Everyone agrees intelligence matters. Few people agree on what good looks like. Even fewer can explain why their current feed helps them make better decisions when something odd is happening in the network.
Most buyers start with the same assumption. More data means more protection. That assumption rarely survives contact with reality.
Even capable security teams can drown under indicators they never asked for. And smaller teams run circles around better funded peers because they understood what intelligence was for and bought accordingly. The difference is not tooling. It’s clarity.
This blog is written for people who already know the basics. The aim is to talk about how threat intelligence vendors operate, where they add value, and where they quietly fail.
What Threat Intelligence Vendors Actually Sell
Strip away the packaging and most threat intelligence vendors sell three things.
- Collection: Sensors, honeypots, malware sandboxes, scraped forums and telemetry from customers. The quality varies wildly. Volume is easy. Relevance is harder.
- Processing: Deduplication, enrichment and basic correlation. This is where many vendors claim sophistication. In practice, much of it is rules and pattern matching layered on top of large datasets.
- Interpretation: This is the part that matters and the part that is most often thin. Interpretation turns activity into something a human can act on. Who is doing this? Why now? Who should care?
Many vendors do the first two competently. Fewer invest seriously in the third. It is expensive and does not scale neatly.
This is why two feeds can contain the same IP address but tell very different stories.
The Quiet Gap Between Intelligence and Action
Most organisations do not struggle to obtain intelligence. They struggle to use it.
Indicators arrive without context. Reports arrive after the incident window has closed. Risk ratings feel arbitrary. Analysts learn, quickly, which feeds can be ignored without consequence.
Over time, trust reduces.
Threat intelligence vendors often respond by adding more – more indicators, more dashboards, more alerts. None of this closes the gap.
The gap exists because intelligence is being treated as a product rather than a capability. A feed cannot know your business. A report cannot understand your constraints. Without adaptation, intelligence remains external commentary.
This is not a tooling failure. It is a design choice.
A Simple Way Intelligence Should Flow
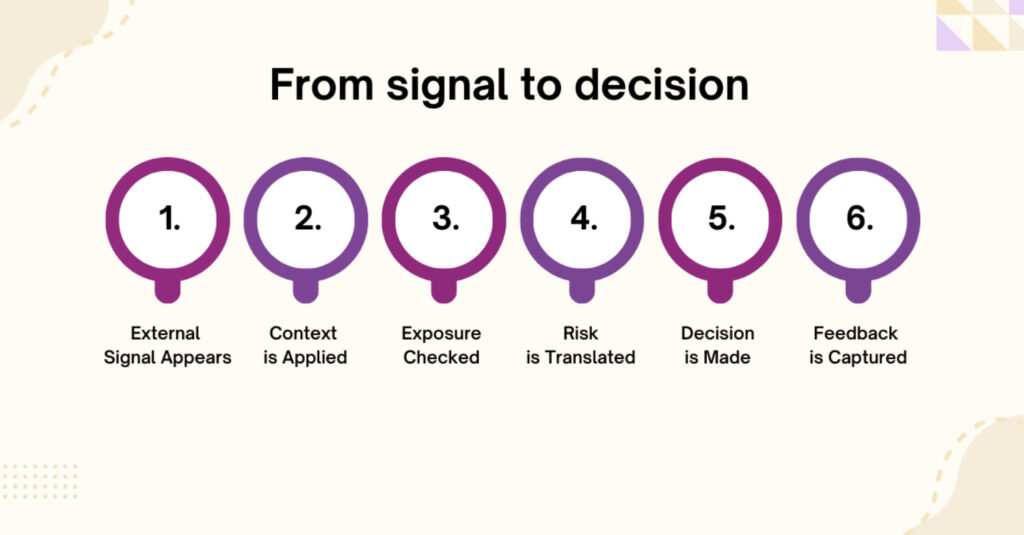
The flow is not complicated, but it is rarely implemented cleanly:
- External Signal Appears This could be malware infrastructure, a campaign report, or a shift in adversary behaviour. At this stage, it is noise with potential.
- Context is Applied Sector relevance, geography, technology overlap, and threat actor intent are assessed. Most feeds stop short here.
- Internal Exposure Checked Do we run the affected stack. Do we see related activity. Has this actor touched us before.
- Risk is Translated Not a score, but a statement. What could realistically happen if this is ignored.
- Decision is Made Monitor, hunt, patch, block, escalate, or deliberately do nothing.
- Feedback is Captured Was the intelligence useful. Was it timely. Did it change behaviour.
Most threat intelligence vendors focus heavily on step one and two. The value appears when steps three to six are supported, even indirectly.
Vendor Differentiation is Subtler Than Marketing Suggests
Datasets overlap more than vendors admit. Many source from the same places, directly or indirectly. The differences tend to appear elsewhere.
Analyst access is one. Can you speak to someone who understands your environment and remembers previous conversations? Or are you limited to ticket queues and generic briefings?
Timeliness is another. Some vendors are excellent at strategic reporting but slow at tactical updates. Others are fast but shallow. Neither is wrong. The mistake is buying the wrong type for your operating model.
Then there is bias. Every vendor has one, whether they acknowledge it or not. Some overstate nation state activity. Others underplay it. Some inflate confidence levels to appear decisive. Learning these patterns takes time.
Framework alignment also matters. Vendors that map cleanly to models like MITRE ATT\&CK can make life easier for detection and response teams. Mapping alone is not insight, but it can reduce friction.
When Intelligence Becomes Shelfware
Shelfware is rarely obvious at purchase time.
It appears six months later when reports go unread. When feeds are piped into platforms no one checks. When analysts stop referencing intelligence during investigations.
This happens for predictable reasons.
The intelligence does not align to business risk. It is too generic or too distant from the organisation’s threat profile.
The delivery model does not match the team. A small SOC does not need weekly strategic briefings. A mature threat team will outgrow raw indicator feeds quickly.
There is no ownership. Intelligence arrives but no one is accountable for turning it into action.
Threat intelligence vendors cannot solve these problems alone, but they often sell as if they can.
Buying Intelligence Without Buying Illusions
Procurement processes tend to reward polished demos. Intelligence rarely shows its weaknesses in a sales call.
A better approach is slower and less comfortable.
Ask to see outdated intelligence and how it was corrected. Ask how often analysts disagree internally. Ask what customers stop using first.
Look for vendors willing to say no. No, this feed will not help you. No, this report is not relevant to your sector. No, we cannot be real time on that topic.
Those answers usually indicate maturity.
Also consider how intelligence will be operationalised. If it sits outside detection engineering, incident response, and risk conversations, it will decay.
Where Services Matter More Than Feeds
Many organisations eventually realise they do not need more intelligence. They need help applying it.
This is where services quietly outperform platforms.
Threat hunting guided by current adversary behaviour. Exposure assessments tied to active campaigns. Intelligence briefings translated into board language without losing accuracy.
These activities require people who understand both the threat landscape and the client environment. Not many threat intelligence vendors invest deeply here, but those that do tend to retain customers longer.
Conclusion
Threat intelligence vendors are not interchangeable, despite how they are often treated. The difference is not who has the biggest dataset. It is who helps you make better decisions with less effort and less noise.
Intelligence should reduce uncertainty. When it increases it, something is wrong.
Organisations that get value from intelligence tend to be deliberate. They know why they are consuming it, who it is for and how success is measured. They also accept that some intelligence will be ignored by design.
This is where experienced partners matter. CyberNX can help you here. They work with organisations and offer a comprehensive threat intelligence feed. They can provide you with real-time insights into emerging threats, vulnerabilities and attack trends.
When intelligence starts changing decisions instead of filling inboxes, you are working with the right model. The vendor becomes secondary. The outcome does not.