In today’s digital landscape, the telecommunications sector stands as a critical pillar of national infrastructure, making it a prime target for increasingly sophisticated cyber threats. My experience working within this space has consistently highlighted the urgent need for robust, proactive cybersecurity measures. The sheer volume of data, the complexity of networks, and the constant evolution of adversarial tactics demand a strategic shift from reactive defense to intelligent, automated protection.
The challenges are multifaceted: from navigating stringent regulatory mandates like the UK’s Telecoms Security Act (TSA) to managing billions of events monthly and thousands of alerts. Relying solely on manual processes is no longer sustainable. It leads to resource drain, delays in detection, and a reactive posture that simply can’t keep pace. This is where the power of cybersecurity automation with n8n has truly transformed our approach, delivering not just efficiency but also significant financial savings and enhanced protective capabilities.
The Unyielding Pressure on Telco Cybersecurity
The telecom industry faces unique pressures. Gartner research indicates that the average cost of a data breach in telco has surged to $5.72 million, placing it as the third most vulnerable sector globally, right after finance and healthcare. This vulnerability is compounded by the escalating frequency and complexity of cyberattacks, a trend expected to intensify with the widespread adoption of AI by malicious actors.
As a network provider, we have a clear mandate: to protect our infrastructure and assets. The Telecoms Security Act (TSA) specifically underscores this by stipulating more comprehensive and extensive logging and monitoring requirements. This means more assets need to be logged centrally, data retained for much longer (e.g., 13 months instead of 90 days), leading to an exponential increase in data volume, types, and consequently, alerts. With our teams already processing 3 to 5 billion events and thousands of alerts monthly, the manual handling of these processes was rapidly becoming a significant bottleneck, threatening to overwhelm our resources. We needed to work smarter, not just harder.
Discovering the Right Automation Platform: The n8n Advantage
Our journey towards smarter cybersecurity began with exploring various Security Orchestration, Automation, and Response (SOAR) options. We initially looked at traditional SOAR tools like IBM Resilient and Tines. While capable of addressing specific SOAR challenges, they often fell short in providing the broad workflow automation capabilities we desperately needed. Our scope extended beyond just security; we needed a platform that could integrate seamlessly across diverse systems and handle complex, end-to-end operational workflows.
We then pivoted to low-code/no-code platforms such as OutSystems, Mendix, and even Power Automate. These tools offered great workflow capabilities but lacked the security-centric focus essential for our specific needs. It was then that we discovered n8n, a platform that uniquely combined robust SOAR capabilities with powerful workflow automation, all within an intuitive low-code environment, while still allowing for custom code when necessary.
What Made n8n Stand Out?
- Dual Capability: It offered both SOAR and general workflow automation.
- Low-Code Flexibility: It provided a low-code model that drastically sped up development, alongside the ability to incorporate Python or JavaScript for more complex integrations or logic.
- Modular Design: This was a game-changer. Instead of building monolithic, end-to-end workflows, n8n enabled us to create reusable modules. For instance, a common email notification module could be built once and then reused across dozens of different workflows, not just within our team but potentially across the entire organization. This modularity drastically reduced duplication of effort and accelerated development.
- Speed of Implementation: Given the urgency of our challenges, we couldn’t afford to wait. The modularity and ease of integration allowed us to rapidly deploy solutions.
Partnering for Accelerated Success: The Role of Bounteous
To accelerate our adoption and implementation of n8n, we sought an experienced partner. After evaluating several options, we chose Bounteous as our accelerator. Their team demonstrated a deep understanding of our requirements, offering flexibility in approach and, crucially, taking ownership of the discovery, solution creation, and even the management of the n8n infrastructure. This partnership was vital, as our in-house engineers were already stretched thin. Bounteous helped us quickly build out the flexible and reusable solutions we envisioned.
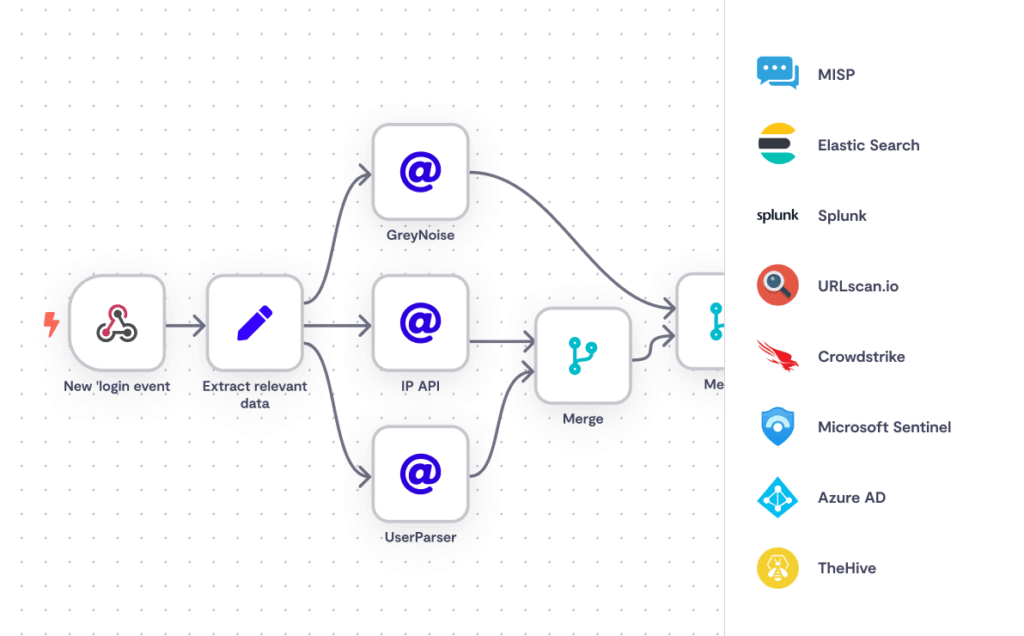
n8n in Action: Crafting Resilient Cybersecurity Workflows
The n8n platform is designed with a visual canvas that makes workflow building highly intuitive. Each operation in a flow is represented by a block or “node.” This visual approach allows both technical and non-technical users to participate in workflow design, fostering co-creation between business and technical teams.
Key Features in Practice:
- Modular Blocks (Orange Arrows): These are the reusable components, like the email sub-workflow or database upsert operations, which ensure consistency and reduce development time.
- Code Blocks (Yellow Curly Brackets): For scenarios where built-in low-code nodes aren’t sufficient, n8n allows for custom Python or JavaScript code, including the ability to import external libraries. This flexibility ensures no task is out of reach.
- Low-Code Blocks (Green Loops): These are pre-built, drag-and-drop nodes that handle common operations, making rapid development possible.
Anatomy of an Alert Resolution Workflow (e.g., using Cabana):
Consider a workflow designed to resolve security tickets more quickly and efficiently, starting with a Cabana alert.
- Ingestion & Initial Action: The workflow is triggered by an alert. An n8n node immediately marks the case in Cabana as “in progress.”
- Human-in-the-Loop Interaction: An email is sent to the relevant subject matter expert (SME) with “Yes” or “No” buttons. This integrates a critical human decision point into the automated flow.
- Dynamic Form Generation: Clicking “Yes” or “No” directs the SME to an n8n-generated form, allowing them to add comments and submit their decision. This form is hosted and managed by n8n, streamlining the feedback loop.
- Automated Response & Closure: Based on the SME’s input, the workflow triggers the next set of actions. If the alert is deemed legitimate, an email might be sent to a remediation team, and the case in Cabana is automatically updated and closed, with all comments logged. This dramatically reduces the time from detection to resolution.
Beyond Alert Resolution: Proactive Monitoring and Fraud Detection
Our n8n implementation extends far beyond incident response. For example:
- Data Feed Monitoring: As part of TSA compliance, we have numerous data feeds that must be continuously operational. We built a workflow that checks the status of approximately 50 critical feeds every 5 minutes. If a feed drops, the workflow performs basic triage to identify the cause (e.g., our side vs. user side). If it’s a known issue, it attempts automated remediation. If not, it escalates to a manual flow. This proactive monitoring was previously impossible to achieve manually at this frequency and scale.
- Fraud Detection: We’ve developed workflows that provide IP geo-location and fraud detection services, helping to localize content, enhance security, and identify suspicious online activities.
- Malware & Vulnerability Detection: Workflows analyze network requests, checking for phishing attempts, suspicious redirects, and other cyberattacks against blacklists and known vulnerabilities.
The DevOps Dimension: CI/CD with n8n
One of the less obvious but equally crucial aspects of n8n is its support for a robust CI/CD (Continuous Integration/Continuous Delivery) pipeline in a low-code environment. Bounteous leveraged n8n’s environment capabilities to create distinct stages for development, testing, and deployment. This allowed us to:
- Version Control: Track changes and roll back if necessary.
- Secure Deployment: Easily and securely update workflows across environments.
- Log Streaming: Monitor workflow execution and troubleshoot effectively.
This structured approach ensured that our automation solutions were not only powerful but also stable, maintainable, and scalable.
Quantifiable Impact: £2.2 Million in Savings and Enhanced Capability
The results since we fully launched our n8n capability in August 2023 have been nothing short of transformative.
- Workflows Deployed: We have launched 33 distinct workflows, along with numerous sub-workflows, with many more in the pipeline. These cover logging, monitoring, SOAR, onboarding data feeds, and even content creation within cyber prevention engineering.
- Enhanced Monitoring & Proactiveness: Our ability to monitor and perform checks has drastically improved. The feed monitoring workflow alone highlights this: a task that would take 10 minutes per feed manually (making frequent checks impossible) is now fully automated and runs every 5 minutes. This has shifted us from a reactive to a highly proactive stance.
- Resource Optimization: The automation has supported our SOAR, SOC (Security Operations Center), and engineering teams, as well as our data onboarding and content creation efforts. We’ve significantly increased our monitored assets (by approximately 50% in two years) without needing to proportionally increase our SOC team size. This means we’re handling more alerts, more quickly, and with greater simplicity.
- Reusability & Speed: The modular nature of n8n means that any integration (e.g., with IBM Resilient for ticketing) or common module (like email) can be reused instantly. This has exponentially increased the speed at which we can generate new workflows and deploy them. We can now provide architectural blueprints and base sets of modules to other teams across Vodafone, enabling them to achieve similar benefits without repeating the initial hard work.
- Massive Savings: Since August 2023, the implementation of n8n has directly saved us approximately 5,000 person-days. Over 3,000 of these are directly related to SOC use cases. In financial terms, this translates to an avoided cost of around £2.2 million to date. Looking ahead, we anticipate continued savings of approximately £300,000 per month.
These figures underscore a fundamental shift: we are working more efficiently, more intelligently, and freeing up our highly skilled analysts and engineers to focus on higher-value, strategic work, ultimately enhancing Vodafone’s ability to protect the UK, our employees, and our customers.
The Future is AI-Powered: Vodafone’s Roadmap
No discussion about the future of cybersecurity is complete without addressing Artificial Intelligence. While AI will undoubtedly empower adversaries, increasing the frequency and sophistication of attacks (think deepfake video scams and advanced phishing), it also offers an unparalleled opportunity for defenders.

AI as a SOC Ally:
- Enhanced Analyst Efficiency: AI can act as a “co-pilot,” making human analysts more efficient by automating data enrichment, categorization, and suggesting next steps.
- Automated Incident Response: AI agents can learn from past successful and unsuccessful incident responses, dynamically creating customized playbooks for every attack scenario. For example, an “MITRE agent” can analyze Jira tickets, identify relevant MITRE ATT&CK techniques, and suggest remediation steps, or even automatically trigger parts of the response.
- In-house Tool Building: The rise of “vibe coding” and AI-assisted development (like Replit Cursor) is lowering the barrier to building custom security tools. In a world where an engineer can build a tailored tool in a day or two, companies will increasingly move towards in-house development of AI-powered security tooling, rather than relying solely on off-the-shelf solutions.
Vodafone’s AI Vision:
Our roadmap for cybersecurity automation with n8n is closely intertwined with AI:
- Continuous Workflow Enhancement: We will continue to enhance our existing workflows, gradually building out capabilities towards full remediation, moving beyond just identification, triage, and alerting.
- Platform Expansion: We are extending the n8n platform’s use across all of cyber prevention engineering, not just SOAR. This includes setting up additional instances, potentially exploring on-premise hosting options, and expanding into new security domains.
- AI Adoption: This is the most exciting frontier. We plan to:
- Utilize native AI tooling within n8n.
- Integrate n8n with our own Large Language Models (LLMs) to automate existing playbooks.
- Incorporate AI into our broader automation frameworks.
It will be a busy year, but the goal is clear: to leverage AI to our advantage, combating increasingly intelligent threats by making our defenses equally intelligent and adaptive. The challenge isn’t primarily about AI adoption or skills (people are eager to learn); it’s about how we can effectively use AI to protect against new forms of attack, such as deepfake social engineering and AI-powered hacking kits.
Key Takeaways for Cybersecurity Automation
Our journey with n8n and Bounteous has yielded invaluable insights:
- Collaboration is Key: Success hinges on strong collaboration across security teams, integration partners, and platform providers.
- Co-creation: n8n’s intuitive interface enables both business and technical teams to co-create solutions, bridging the gap between operational needs and technical implementation.
- Modular Design for Scale: Adopting a modular workflow design simplifies maintenance, allows for rapid iteration, and ensures consistency across complex automations. This is critical for scaling efforts.
- Real-World Application: Applying automation to real-world cyber challenges (threat detection, response, proactive monitoring) provides practical insights into its power and helps address limitations as the threat landscape evolves.
Conclusion
The transformation of cybersecurity operations through intelligent automation is not just a theoretical concept; it’s a tangible reality that delivers immense value. My experience has shown that by embracing platforms like n8n and fostering strategic partnerships, organizations can significantly enhance their defensive posture, reduce operational costs, and free up invaluable human talent to focus on complex, high-impact tasks. The journey is ongoing, particularly as we integrate the accelerating power of AI, but the foundation laid by robust cybersecurity automation with n8n has already revolutionized how we protect our critical assets and serve our customers.